Remote Access Tool
Posts in category: Remote Access Tool
A cross-platform remote access tool (RAT) attacking Windows, Linux and macOS operating systems. The malware is a java file and therefor can be executed on different OS.Apparently, in 2016 the malware added the macOS support. On execution it will create a LaunchAgent so it will survive a system reboot.The malware is able to download and execute additional malicious files, execute remote commands and collect and send data from infected machine.In September 2018, new Adwind campaign was discovered attacking macOS, Windows and Linux OS, which was mostly targeting users in Turkey, as the document used in the campaign was written in Turkish.The payload in this campaign was Adwind RAT version 3.0.
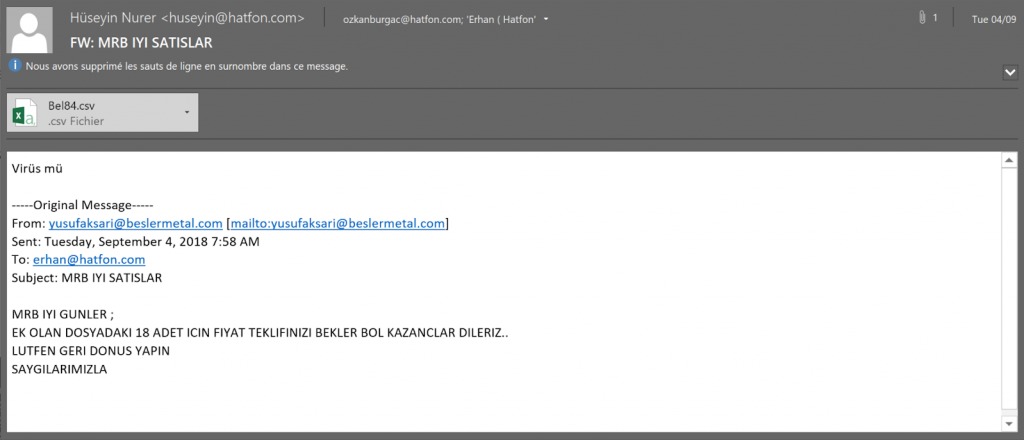
Source: talosintelligence
Links:
Samples:
d8b426700c3c10413abb8acdcfeccaaec8f06cd9
Coldroot was first published as an open source RAT for macOS on Github on 2016, but no real malware was discovered until 2018. The malware is weaponized with a wide range of commands such as:- File/Folders control (move, reanme, delete) – Remote Desktop – Download, upload and executes files – Process control (list, execute, kill) – Taking screen shots – Gain accessibility rights by modifying TCC.db – KeyloggingThe malicious application arrives with a normal “document” icon, so a user might think he is opening a document rather than a malicious application.
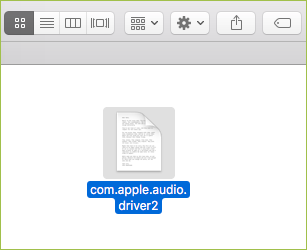
Source: Digita Security
Once executed, the malware will try to get root access via popping a window asking the user for credentials. It will create a LaunchDaemon in order to persist system reboot (“/Library/LaunchDaemons/com.apple.audio.driver.plist”). The malware keep its configuration within a file in its application bundle (“MacOS/conx.wol”). We can see below its content:
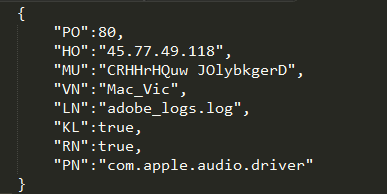
Source: Digita Security
In addition it will modify the system security database file TCC.db to add itself as Accessibility application, meaning it will then have the ability to control the computer.
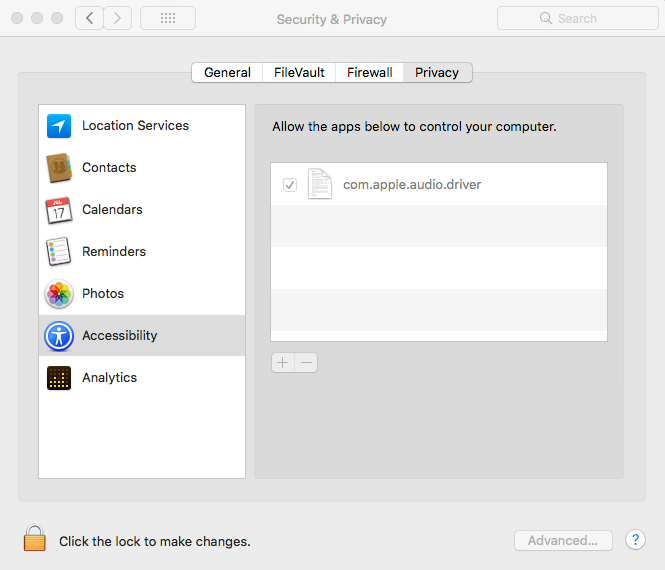
Source: Digita Security
Links:
Samples:
7e60c8ae77e20fbd7699187d0baf9ed0477e72f3
EggShell is an open source post exploitation surveillance tool written in Python. Its target operating systems are macOs and IOS, and recently basic support for Linux was added.
It gives the person who controls it an extended list of commands and includes uploading & downloading files, taking pictures, shell command execution, persistence, password retrieval and more. The full list is below:
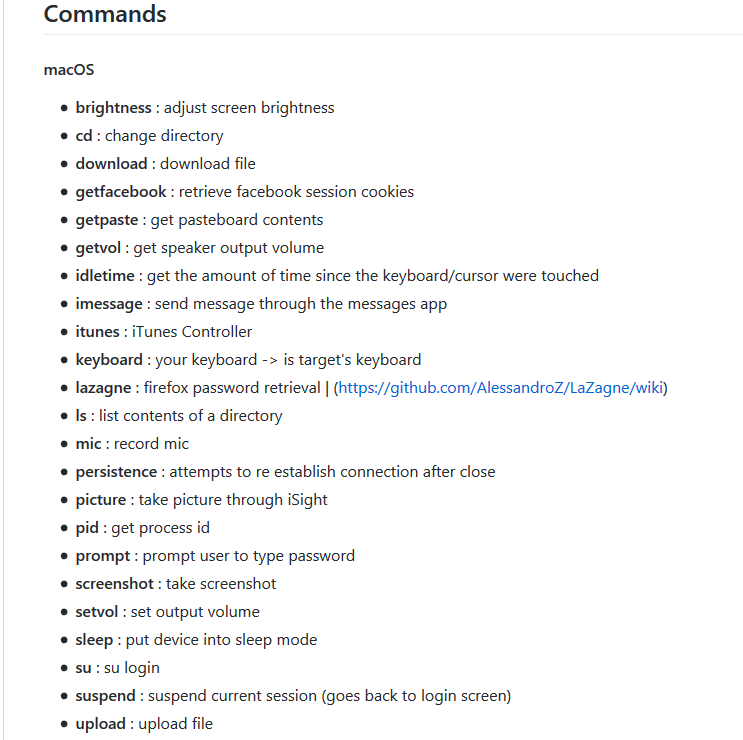
Links:
An open source Remote Administration Tool (RAT) for macOS/ OSX that was published on Github in 2018. EvilOSX is written in Python, and according to the developer the motivation behind it was that it will be used in “Rubber Ducky”. A USB mostly used by hackers to inject keystrokes to a computer is connected and with that bypasses the need to enter credentials on the login screen.
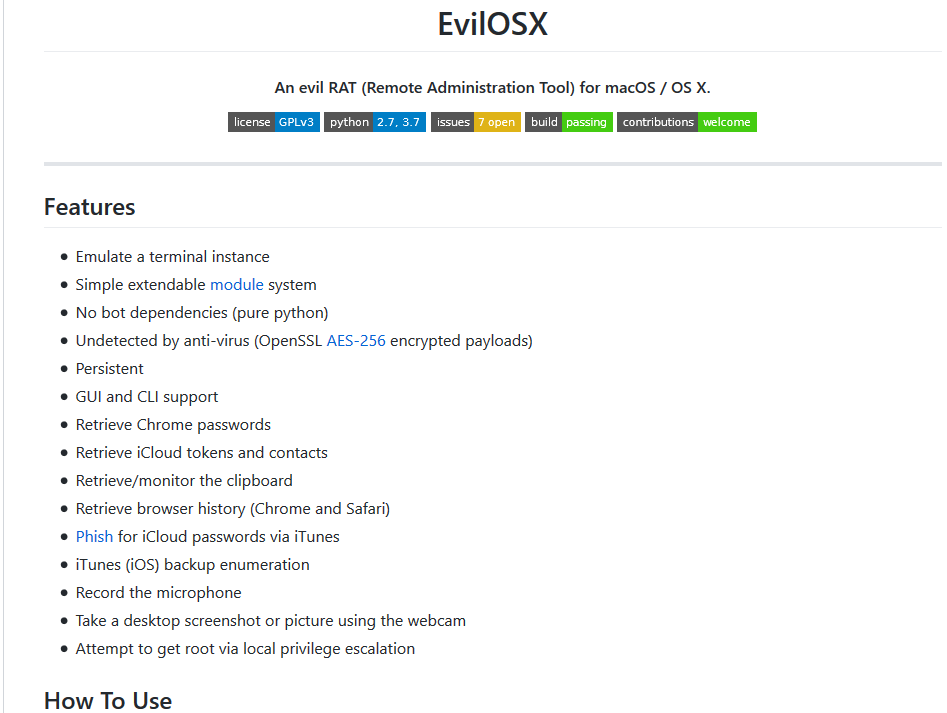
Since it is open source, it may be used by anyone for different uses that it was mainly created. Some of its abilities it can perform on the system include:- Steal password from Chrome – Steal iCloud tokens and contacts – Collect browsers history – Record the microphone – Take screenshots or pictures with webcamThe full capabilities list is below:
On the server side (C&C), the EvilOSX will show the list of bots and available commands to perform remotely on each one of them:
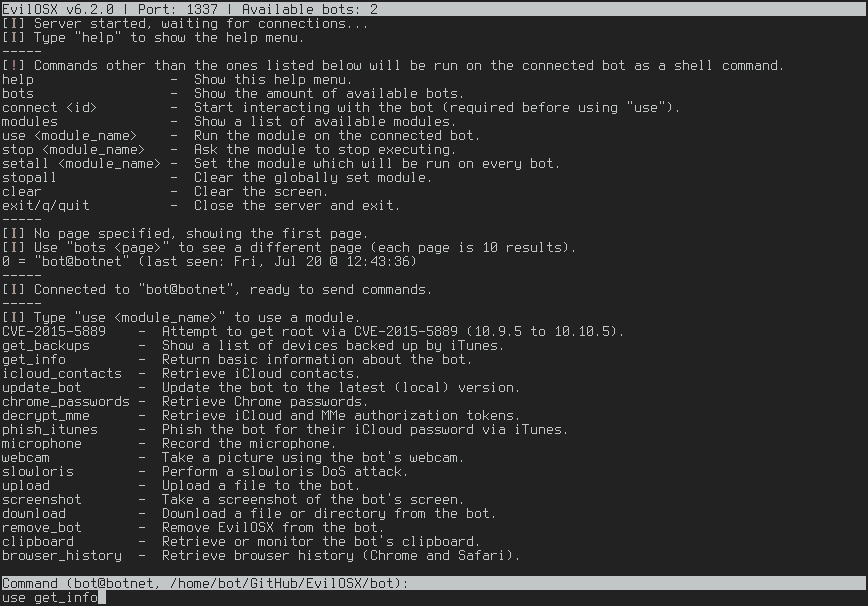
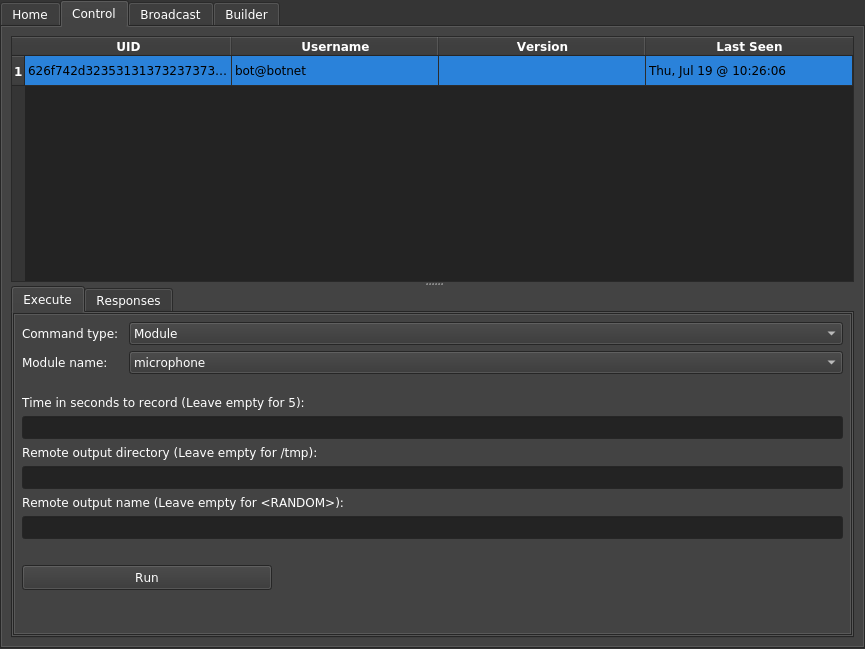
Links:
Samples:
e4d7bce2a6900424e62bfc9a871382b56aaa510a
Proton is a Remote Access Tool for macOS. It was first published as a service in a Russian cybercrime forum and later variants of this malware were seen spreading in different ways.
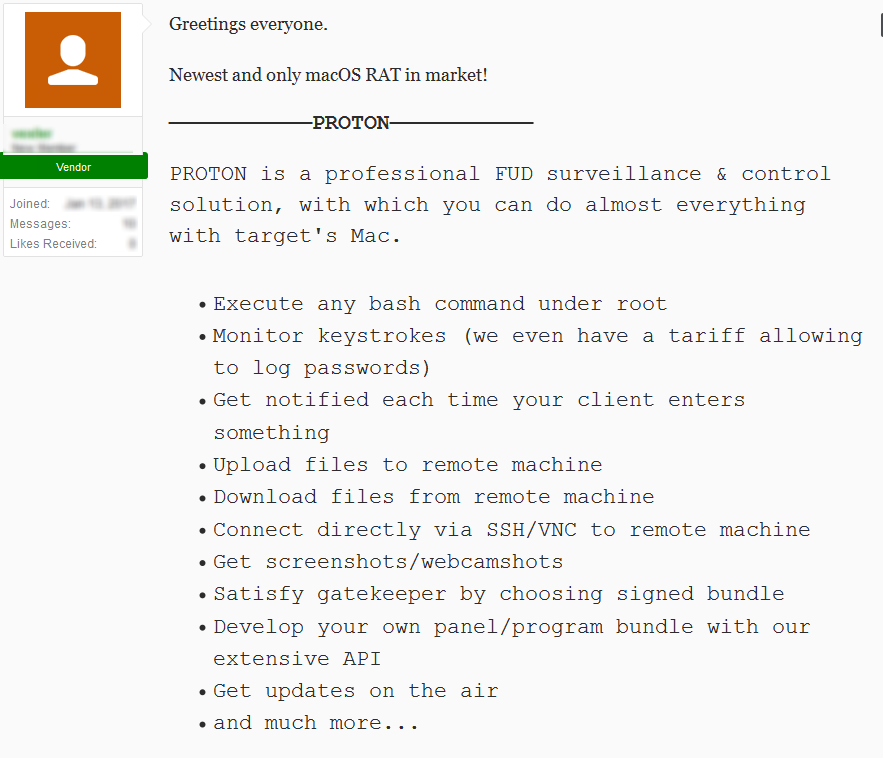
Source: SIXGILL
Over time, researchers have discovered different applications containing the Proton malware. One of them was as a fake “Symantec Malware Detector”. Another was within a package of the “Elmedia Player” application which was somehow repackaged with the malware.

Source: Malwarebytes
The malware will pop a message asking the user for credentials to gain root privileges on infected machine. To persist it creates a LaunchAgent to start itself after reboot. The malware has a wide range of commands available such as:
- Keyloggin – Passwords and data stealing – Remote access – Copy/Create/Delete files on infected machine – Download, Upload, Execute files – More…
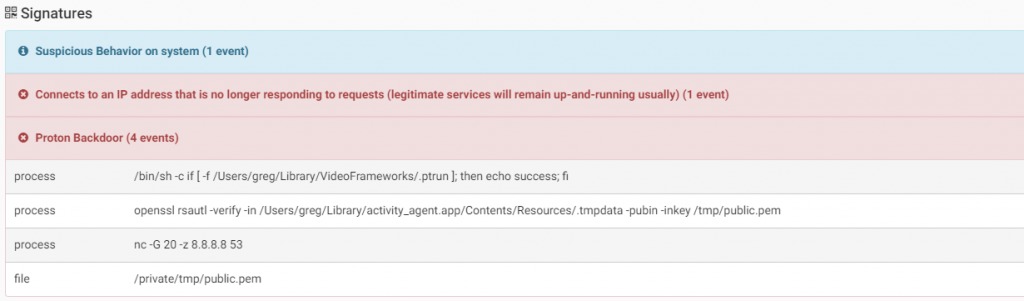
Source: CheckPoint
For more details about Proton and its variants click on the links below.
Links:
- PROTON – A NEW MAC OS RAT
- HandBrake Hacked! - osx/proton (re)appears
- PROTON.B: WHAT THIS MAC MALWARE ACTUALLY DOES
- OSX/Proton spreading again through supply-chain attack
- OSX.Proton spreading through fake Symantec blog
- OSX/Proton Malware is Back! Here’s What Mac Users Need to Know
Samples:
0935a43ca90c6c419a49e4f8f1d75e68cd70b274
8cfa551d15320f0157ece3bdf30b1c62765a93a5
A cross platform malware affected not only macOS but also Windows and Linux operating systems. Wirenet, a trojan that opens a backdoor on an infected machine, is also able to take screenshots and collect users keystrokes and additional data from the system and send it to attacker’s server.The malware steals user’s data and passwords for different programs such as browsers (Opera, Firefox, and Chrome) and other popular internet applications such as Thunderbird and SeaMonkkey.
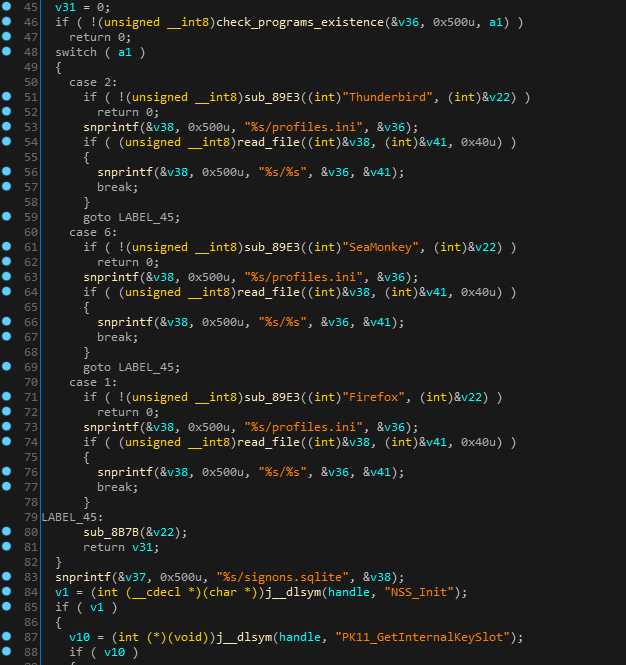
The malware installs itself in the folder %home%/WIFIADAPT.app to communicate with its C&C and encrypts the data using AES encryption algorithm.
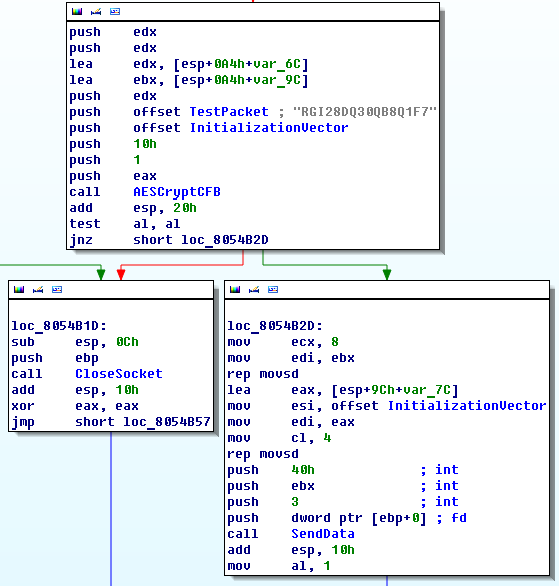
Source: Dr.WEB
Links:
- The first Trojan in history to steal Linux and Mac OS X passwords
- Wirenet: The Password-Stealing Trojan Lands on Linux and OS X
Samples:
c520e9099bfc695b54662bdb7e8fa5b2800a72e9
c36f0943484ce8f8aba2d649aae2ad1243947c4e
1f0a890b3ac0daf93e6de8f7e93559355780ba84